
As a member of the IT world, it's unlikely you will not have heard of the Meltdown and spectre chip-level exploit saga, however, if you have somehow managed to dodge the media coverage of this particularly controversial security flaw, or want a refresher, then allow us to summarise it for you now.
Meltdown and Spectre exploit critical vulnerabilities in practically all modern processors. These hardware vulnerabilities allow programs to steal data which is currently being processed on the computer. While programs are typically not permitted to read data being held for other programs, a malicious program can exploit Meltdown and Spectre to get hold of secrets stored in the memory of these other running applications. This might be useless information but equally could include passwords stored in a password manager or browser, your personal photos, emails, instant messages or even business-critical documents.
Meltdown and Spectre exploits work on servers, personal computers, mobile devices and those systems running the cloud. That means that depending on the cloud provider's infrastructure, it might even be possible to steal data from other cloud users; a frightening prospect!
Meltdown and Spectre are chip-level exploits, which are within the processor design, and cannot be patched out by a simple software solution. Equally, this will also mean malicious activities within your system may not show in system logs since this can be done at a very low level.
Ah, sounds worrying - how do we baton down the hatches and fix these exploits?
Meltdown
Well, first it’s important to know that meltdown is currently only known to impact Intel microprocessor range from around 1995 onwards, with the exception of Intel Itanium and Intel Atom CPUs from before 2013. No AMD processors are known to have the Meltdown exploit to date.
You can see some examples of a meltdown in action at the following links, and how simple it could be to steal information in just a few minutes -
Currently, kernel/core patches are available for most operating system variants and have already been made available mainstream through the built-in update processes, meaning if you are up to date then it’s likely you will already be covered.
There has however been some press around AMD systems being negatively impacted by meltdown patches, but this is simply down to poor programming all round; in short, the patches did not check which processor architecture it was being applied to (whether it was Intel or AMD) and operated regardless of whether they were necessary or not. This appears to have been solved and later updates do consider AMD processors better, although some operating systems failed to boot due to this error with the earlier patch, causing considerable pain for those users.
Spectre variant 1 & 2
Spectre exploits the speculative execution carried out by processors from AMD, Intel and Arm. They have technical differences between all their products, but the general premise of the feature is that the cores speculate what’s needs to be processed in future cycles and execute those jobs ahead of time, rather than waste cycles idling. Those speculative calculations can unwittingly expose areas of system memory which the original program is not privileged to access.
“Spectre breaks the isolation between different applications. It allows an attacker to trick error-free programs, which follow best practices, into leaking their secrets. In fact, the safety checks of said best practices actually increase the attack surface and may make applications more susceptible to Spectre” - Reference from www.meltdownattack.com
Spectre variant 3a&4
As of May 22nd 2018: Intel announced a new disclosure on the Side Channel (Spectre/Meltdown) security vulnerability. This issue has a 4.3 Medium CVSS rating. This fix will address Variant 4 and another issue called Variant 3a. You can see the detailed statement here.
If your systems have been patches for spectre 1+2 plus meltdown then the good news is that it makes exploiting spectre 3a and 4 that much harder to achieve. However, increasing difficulty level is not the same as fixing the issue and this will be addressed by Intel.
AMD has yet to confirm as of whether 3a and 4 variants impact their architectures.
Could my systems be affected?
Almost certainly, but there are patches to help. To check if you are susceptible to either attack there are scripts publicly available to check if your relative OS is patched and if your system is, therefore, susceptible to meltdown or spectre.
Linux: https://github.com/speed47/spectre-meltdown-checker
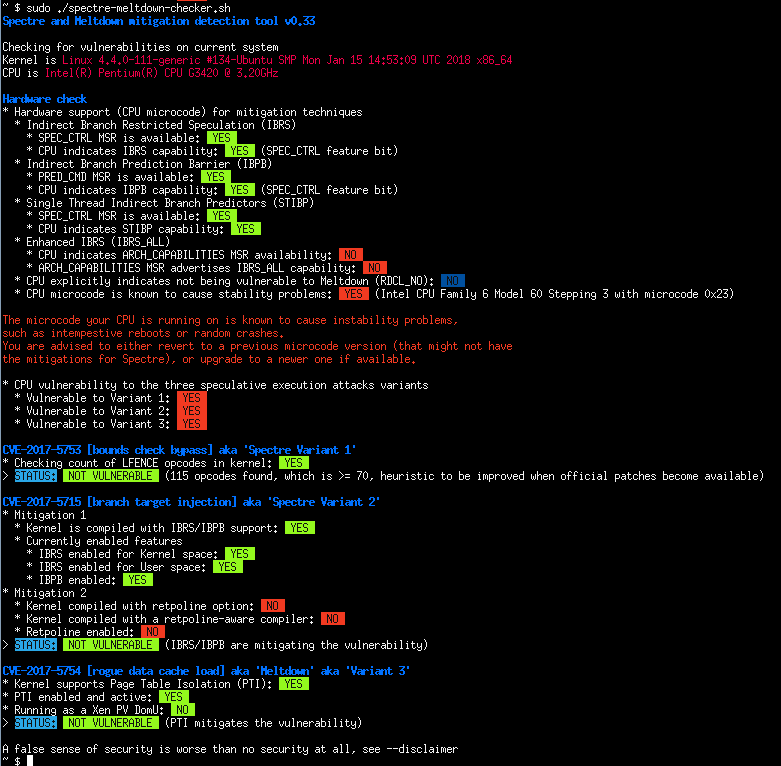
Windows: https://gallery.technet.microsoft.com/scriptcenter/Speculation-Control-e36f0050
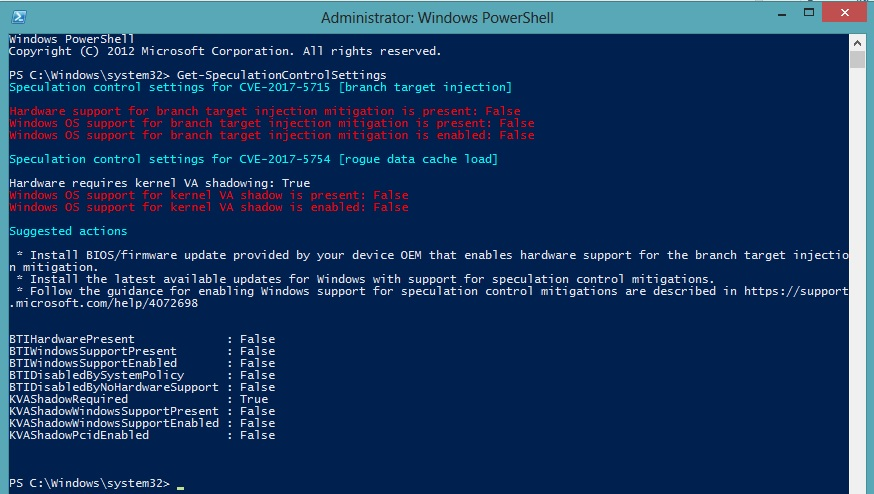
Note, however, that if you are patched, this may result in a potential performance decrease, but if your systems are unpatched, then you could be susceptible to malware built upon these exploits - it's something of a catch 22.
Below, we will go through what (if any) impacts we have seen and how to patch your system.
Solutions and patching across our range
Software Patching
Generally, keeping your OS up to date is the best practice, though in production it’s not always possible to blindly update systems daily or weekly. Therefore for some, it's important to understand which patches fix meltdown/spectre specifically to target this vulnerability and to prioritise them. The current set is listed below for your convenience.
Note, however, that while spectre V2 can be mitigated in software, it cannot be fully resolved with the current generations of hardware.
The solution going forward in the industry is that fixes will be integrated with future processor products from Intel and AMD, although further information on this is covered in the hardware patching section below.
OS – Windows
Windows 7,8,10: https://support.microsoft.com/en-us/help/4073119/protect-against-speculative-execution-side-channel-vulnerabilities-in
Resolving Antivirus issues: https://support.microsoft.com/en-us/help/4072699/january-3-2018-windows-security-updates-and-antivirus-software
OS – Linux
Centos 7: https://lists.centos.org/pipermail/centos-announce/2018-January/022696.html
Debian: https://security-tracker.debian.org/tracker/CVE-2017-5754
Ubuntu: https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SpectreAndMeltdown
For any further operating systems or information that has been listed further information can be found: https://meltdownattack.com/
Hardware Patching
Intel has released their microcode updates intended to address the Spectre Variant 2 issue for the Skylake and Broadwell/Haswell server products. You can find out more about which exact products Intel has released this code for here.
Intel has teamed up for some of the microcode patchings to be completed through windows updates, although processor support is limited as of the date of this article. Moving forward, however, Microsoft plans to create more windows updates that carry out in band microcode updates. For more information see here.
Supermicro is now integrating that microcode into an updated BIOS, before testing/validating that updated BIOS before release.
The Skylake microcode was released first and an initial set of updated BIOS is now available. The Broadwell/Haswell updates will quickly follow.
Supermicro is in the process of applying microcode patches across their range for all systems affected, covering all the elements of the vulnerability which can be via BIOS updates. Note however that these work in conjunction with software-based updates, so be sure to also apply those updates listed above in the software patching section for full coverage.
AMD: https://www.supermicro.com/support/security_Intel-SA-00088.cfm?pg=H11#tab
Intel X11: https://www.supermicro.com/support/security_Intel-SA-00088.cfm?pg=X11#tab
Intel X10: https://www.supermicro.com/support/security_Intel-SA-00088.cfm?pg=X10#tab
Intel X9/X8: https://www.supermicro.com/support/security_Intel-SA-00088.cfm?pg=X9#tab
AMD plans to integrate a hardware chip fix in their 2019 Xen 2 product prior to release, eliminating the loophole altogether.
Intel too plans to bring hardware fixes to their 8th Generation Intel Core series processors and Cascade Lake Xeon, bringing this particular vulnerability to an end.
We hope this article has been useful for you, but should you have any further questions or problems then please get in contact with Boston Labs team.
Research and reference sites:
- https://blog.barkly.com/meltdown-spectre-patches-list-windows-update-help
- https://meltdownattack.com/